
Almost noone!
Or, more accurately, there is no single emergency telephone number where we can call for effective help during or after cyberattacks as we have with physical security. In cyber emergencies, corporate and government help desks and call centers are not of much help.
Still, on a more optimistic note, cybersecurity response spaces are emerging everywhere in tech companies, governments, the insurance industry, and more.
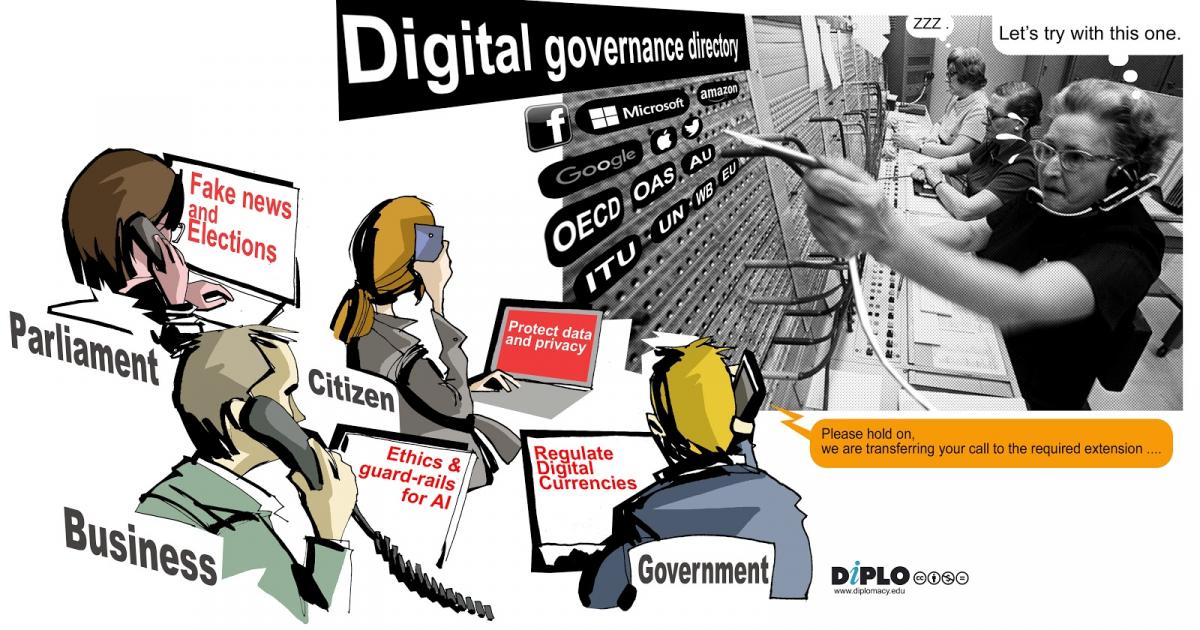
As illustrated below, calls for cybersecurity support will start to be increasingly connected.

The search for the right number and connection for cyber help was in the focus of the lively debate organised by Swiss innovation incubator FONGIT and the Geneva Internet Platform (GIP). The event aimed to link vibrant start-up communities based on the left bank of river Rhone in Geneva with the cybersecurity diplomacy and negotiations happening on the right side of the river.

M. Zard (Proton), D. Rufenacht (InfoGuard), L. García Vargas (Edgelands Institute)
FONGIT’s start-up companies, like all of us, from citizens, companies, and countries, are searching for the answer to the question: Who do you call when you are cyberattacked?
The need for cybersecurity help desks intensifies with our increasing dependence on digital networks. It took human society centuries to develop laws, law enforcement agencies, and courts to protect our lives, rights, and properties. It remains to be seen how long it will take for us to ensure cyber-safety mechanisms and procedures.
Currently, governments cannot ensure reasonable digital security as they can in physical space by protecting our lives, rights and property.
Governments worldwide can’t fulfil the social contract with their citizens! Do we need a new social contract for the digital age, as the UN Secretary-General suggests in his report “Our Common Agenda”?

There are many unanswered questions and large open issues ahead. Yet, we need to address the immediate cybersecurity challenges.
Thus, as it was discussed at the FONGIT/GIP panel meeting, the next steps are to evaluate what has been done so far and what can be done to speed up the creation of a safe digital environment.
What has been done?
Various actors are searching for solutions for digital risks. Here’s a summary of the emerging cybersecurity landscape.
Businesses are responding to rapidly-growing cybersecurity demands.Today, most cyberattack victims will go to specialised companies who can help stop attacks and restore activities. Big tech giants are investing heavily in cybersecurity. Also, there are many small companies and start-ups that provide customised and trusted cybersecurity services.
Tech communities have been developing bottom-up resilience via CERTs (computer emergency response teams) networks worldwide.
Insurance, in the face of cyberattacks, is one of the current solutions available with companies offering cyber insurance packages. But, the field is nascent with many open issues on policies, premiums, and risks.
Governments have also intensified their cybersecurity work, especially in 2022 as geopolitical security risks increased with the Ukraine war and other international crises. On a national level, there is a growing number of legislation, critical response centres, and new cybersecurity initiatives.
On the international level, cybersecurity negotiations happen in different global, regional, and new types of fora. At the UN, diplomats negotiate cybersecurity approaches in the UN Open Ended Working Group (OEWG) working on a cybercrime convention in OEWG dealing with lethal autonomous weapons (LAWS).
New multistakeholder approaches that bring together governments, businesses, and academia include: the Paris Call for Trust and Security in Cyberspace initiated by Microsoft and France, the Christchurch Call to stop terrorist and violent extremist content online after the terrorist attack in New Zealand, and Microsoft proposed the Digital Geneva Convention as a solution for cybersecurity challenges.
Organisational cultures and procedures are the main challenges. With businesses, governments, and other organisations, there are many gaps in ensuring a cybersecurity culture. Even if there are available policies, they are often unobserved.
Individual users are often the weakest link in cybersecurity protection. More simple ‘cyber hygiene’ measures are needed to avoid trivial mistakes such as writing passwords next to the computer, not updating anti-virus software, and being careless while using online resources. Cybersecurity awareness building and education are needed on all levels of society from local communities to schools and companies.
What can be done?
All actors from citizens to companies and countries play essential roles in effective cybersecurity solutions. However, the cybersecurity landscape will take time to develop while calls for help will become increasingly urgent. As these calls need to be answered immediately, we need a lot of wisdom in developing fast solutions while having a strategic cybersecurity direction. In a way, we have to be ready to sprint, by answering immediate problems, and run a marathon, as we develop a cybersecurity landscape.
In International Geneva, around the two banks of the river Rhone, businesses, diplomats, and academics can run this cybersecurity marathon/sprint race.

Important steps were taken during the GIP/FONGIT panel on 5th October 2022. We invite you to join us in the next steps of this complex journey which should answer this rather simple question: Who do you call when you are cyberattacked?
Keep up with the latest cybersecurity updates, 2022 cybersecurity trends, and analysis on the GIP Digital Watch dedicated page!
It is Diplo’s 20th anniversary! Celebrate with us and visit our dedicated page.
Almost noone!
Or, more accurately, there is no single emergency telephone number where we can call for effective help during or after cyberattacks as we have with physical security. In cyber emergencies, corporate and government help desks and call centers are not of much help.
Still, on a more optimistic note, cybersecurity response spaces are emerging everywhere in tech companies, governments, the insurance industry, and more.
As illustrated below, calls for cybersecurity support will start to be increasingly connected.
The search for the right number and connection for cyber help was in the focus of the lively debate organised by Swiss innovation incubator FONGIT and the Geneva Internet Platform (GIP). The event aimed to link vibrant start-up communities based on the left bank of river Rhone in Geneva with the cybersecurity diplomacy and negotiations happening on the right side of the river.
FONGIT’s start-up companies, like all of us, from citizens, companies, and countries, are searching for the answer to the question: Who do you call when you are cyberattacked?
The need for cybersecurity help desks intensifies with our increasing dependence on digital networks. It took human society centuries to develop laws, law enforcement agencies, and courts to protect our lives, rights, and properties. It remains to be seen how long it will take for us to ensure cyber-safety mechanisms and procedures.
Currently, governments cannot ensure reasonable digital security as they can in physical space by protecting our lives, rights and property.
Governments worldwide can't fulfil the social contract with their citizens! Do we need a new social contract for the digital age, as the UN Secretary-General suggests in his report "Our Common Agenda"?
There are many unanswered questions and large open issues ahead. Yet, we need to address the immediate cybersecurity challenges.
Thus, as it was discussed at the FONGIT/GIP panel meeting, the next steps are to evaluate what has been done so far and what can be done to speed up the creation of a safe digital environment.
What has been done?
Various actors are searching for solutions for digital risks. Here’s a summary of the emerging cybersecurity landscape.
The tech sector is responding to the needs of the fast growing cybersecurity industry. Today, most cyberattack victims will go to specialised companies who can help stop attacks and restore activities. Big tech giants are investing heavily in cybersecurity. Also, there are many small companies and start-ups that provide customised and trusted cybersecurity services.
Insurance, in the face of cyberattacks, is one of the current solutions available with companies offering cyber insurance packages. But, the field is in a nascent with many open issues on policies, premium, and risks.
Governments have also intensified their cybersecurity work especially in 2022 as geopolitical security risks increased with the Ukraine war and other international crises. On a national level, there is a growing number of legislation, critical response centres, and new cybersecurity initiatives.
On the international level, cybersecurity negotiations happen in different global, regional, and new types of fora. At the UN, diplomats negotiate cybersecurity approaches in the UN Open Ended Working Group (OEWG) working on a cybercrime convention in OEWG dealing with lethal autonomous weapons (LAWS).
New multistakeholder approaches that bring together governments, businesses, and academia include: the Paris Call for Trust and Security in Cyberspace initiated by Microsoft and France, the Christchurch Call to stop terrorist and violent extremist content online after the terrorist attack in New Zealand, and Microsoft proposed the Digital Geneva Convention as a solution for cybersecurity challenges.
Organisational cultures and procedures are the main challenge. With business, government, and other organisations, there are many gaps in ensuring a cybersecurity culture. Even if there are available policies, they are often unobserved.
Individual users are often the weakest link in cybersecurity protection. More simple ‘cyber hygiene’ measures are needed to avoid trivial mistakes such as writing passwords next to the computer, not updating anti-virus software, and being careless while using online resources. Cybersecurity awareness building and education is needed on all levels of society from local communities to schools and companies.
What can be done?
All actors from citizens to companies and countries play essential roles for effective cybersecurity solutions. However, the cybersecurity landscape will take time to develop while calls for help will become increasingly urgent. As these calls need to be answered immediately, we need a lot of wisdom in developing fast solutions while having a strategic cybersecurity direction. In a way, we have to be ready to sprint, by answering immediate problems, and run a marathon, as we develop a cybersecurity landscape.
In International Geneva, around the two banks of river Rhone, businesses, diplomats, and academics can run this cybersecurity race.
Important steps were taken during the GIP/FONGIT event. We invite you to join us in the next steps of this complex journey which should answer this rather simple question: Who do you call when you are cyberattacked?
Keep up with the latest cybersecurity updates, 2022 cybersecurity trends, and analysis on the GIP Digital Watch dedicated page!
It is Diplo’s 20th anniversary! Celebrate with us and visit our dedicated page https://www.diplomacy.edu/our-story/
Click to show page navigation!




 DiploFoundation
DiploFoundation