Diplo’s webinar on the Apple-FBI case, on 17 March (watch the recording), evolved into a Socratic dialogue on the core concepts and underlying assumptions of the case. The lively debate inspired us to create a series of posts that argue the main dilemmas, played out by three fictitious characters, Privarius, Securium, and Commercias. While the first three posts tackled the main facts, security-related arguments, and privacy and encryption, the fourth conversation looks at privacy, trust, and the economic model. Join us in the debate with your comments and questions.

Securium: Let’s face it though, has Apple really been advocating for the rights of its users, or is this more of a business strategy through which it has tried to regain the users’ trust?
Privarius: While it looks like Apple is in fact supporting privacy, we must not forget that companies are primarily driven by commercial interests. Many – including the FBI – have argued that Apple’s position is more about its business model than the protection of human rights.
Commercias: Even if companies have commercial interests, they can still work hard to protect human rights, including privacy.
Privarius: True. But can we expect businesses to always serve the good cause? Will the protection of human rights always fit into their model, and what if profits drive them to support other causes?
Commercias: It is also a matter of trust. If we look at the Internet business model, we realise how important users’ trust is. Arguably, obeying the court order may lead to diminished trust in Apple, and could provide a market advantage to other products offering strong built-in encryption solutions.
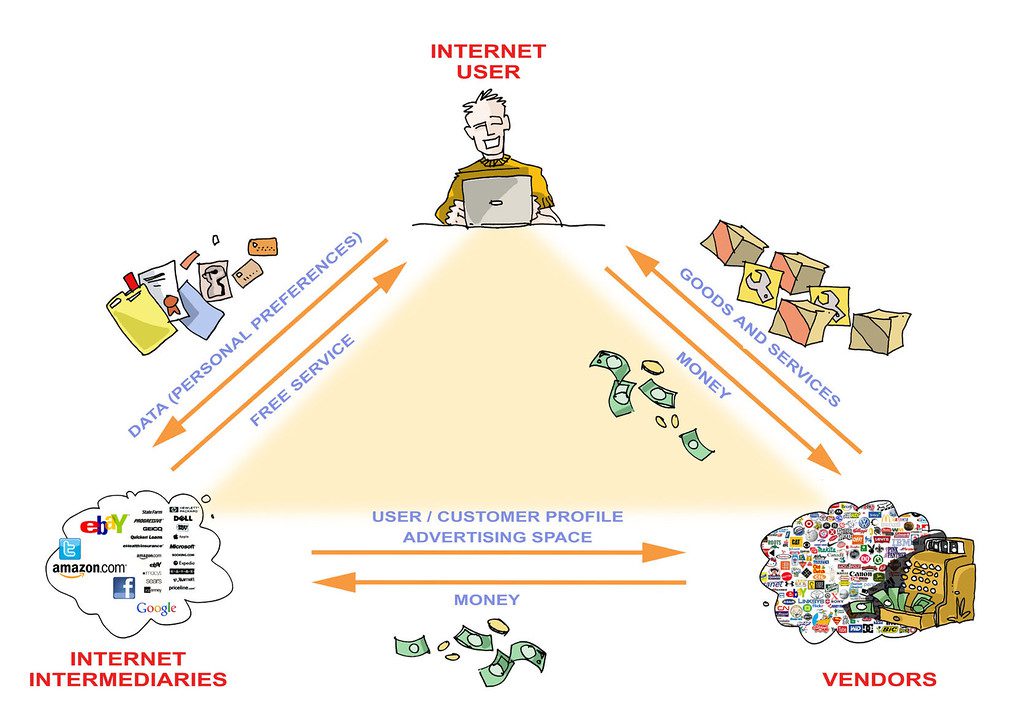
Privarius: So perhaps, if we had to identify Apple’s position in the triangular model, we might say that Apple is both a vendor (selling tech products), and an intermediary (storing users’ data).
Commercias: Indeed. This is probably why Apple took such a strong position in challenging the authorities. Apple’s business model could be seen a somewhat more diverse than, for example, that of Google, Facebook and Twitter, which depend heavily on data. The data-driven Internet industry is quite vulnerable to major policy ‘earthquakes’, such as the Snowden revelations, or the ongoing Apple/FBI controversy. Microsoft is another company that challenged the US authorities (court case on authority over data in Ireland). Just like Apple, Microsoft has a more diverse business model than typical Internet industry companies.
Privarius: And yet, if Apple loses this case, it will further erode the users’ trust in companies too, and not just the security sector. As Edward Snowden tweeted recently: ‘The @FBI is creating a world where citizens rely on #Apple to defend their rights, rather than the other way around.’
Securium: As a result, users will try to find their own ways to protect themselves – through alternative and niche products, online software, etc. In such an environment, only the more skillful citizens will be more protected, while less skillful users will be additionally endangered by criminals and terrorists, which are becoming more and more tech-savvy. We should rather aim to have a minimum level of security for everyone, and to achieve this, end users should not be left to protect themselves through the use of cipher protection….
Privarius: And yet, if governments cannot protect the security and human rights of its citizens – which is the basis of any social contract – citizens should be allowed to protect themselves.
Commercias: Exactly… In real-life, by using guns; in cyberspace by using cipher protection. This is interesting: gun lobbyists and cipher-enthusiasts may share an underlying logic for their actions.
Privarius: The analogy with guns is incorrect; encryption protects, it doesn’t cause damage to others. Connected devices – computers, smartphones, tablets – can do both. Encryption prevents criminals from misusing users’ computers (90% of attacks are based on social engineering, using access to private data to fine-tune and adjust the attacks for phishing or spear-phishing). Encryption also strengthens the security of protocols and online communications in general, making attacks such as ‘man in the middle’ attacks much harder. Not to mention that encryption can save lives – as the UN Commissioner for Human Rights rightly mentioned – lives of activists, journalists, and whistleblowers around the world. Rather than reducing the levels of cybercrime by weakening encryption, the security community needs to look into how encryption can contribute to a more secure Internet…
Securium: Or maybe, we should let the courts decide on the next steps…
The fifth conversation, published on Wednesday, 30th March, will tackle the next steps, including the idea of a new Internet social contract. Stay tuned.